2 months on from WannaCry Ransomware Attack
July 7th will mark 2 months since the Ransomware #wannacry malware attacked systems around the world affecting over 230,000 computers globally. While the HSE were able to avoid serious impact there were still many lessons that could be learnt.
We talked to Fran Thomson, Director responsible for Engagement and Delivery, and Darach Glennon, Director responsible for Customer Service Experience. We reviewed the week and the outcomes that have been learned.


The
On the afternoon of Friday the 12th May while the Digital Health Governance Group were meeting reports began coming in from the media and contacts within the NHS of the attack on global IT infrastructure by the ransomware
The ultimate goal was to protect patient care and every decision was centred around that. The priorities became: secure the internal network and access, consider external vulnerabilities and manage the wider health sector information systems. The strategy throughout the process was to ensure that communications were clear and frequent to all affected by the event. This was to ensure that everyone was aware of processes and updates as the incident unfolded.
That evening and over the weekend teams were mobilised across the country. Different teams were assigned different strands of the emergency work and communicated through conference calls that were initially happening every two to four hours. There were multiple actions taken in response to this multi-faceted problem. These can be seen in the figure below.
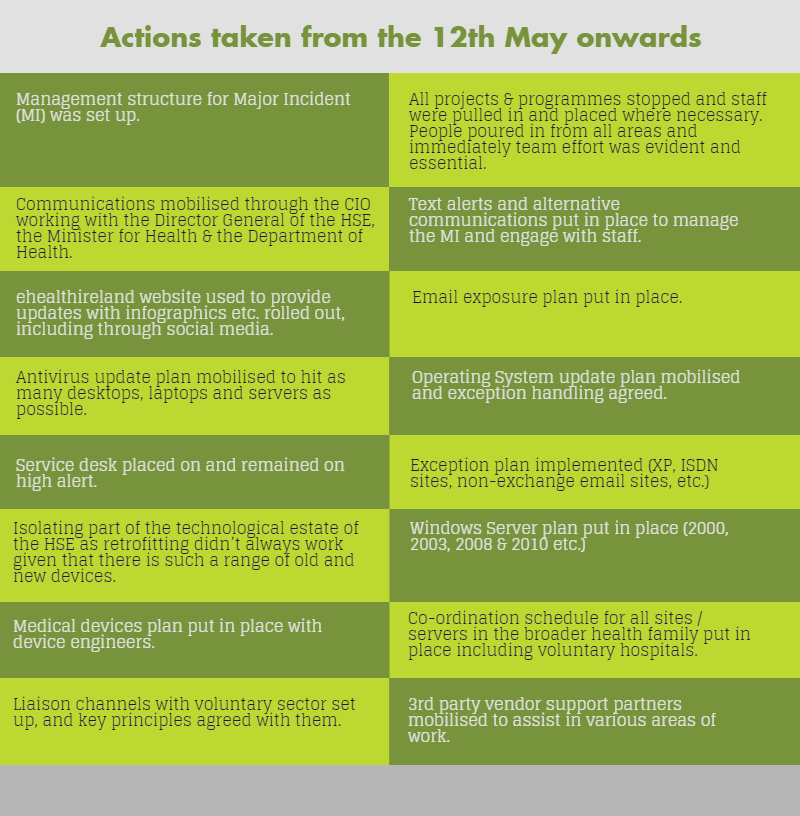
The aim over the weekend was to ensure that the information systems could be turned on where ever possible on Monday morning and minimise any disruption to patients and users. It was imperative that this message was communicated to the wider health service, to make sure they were aware of the attack, were confident that it was being dealt with and knew what steps they should take when they returned to work on Monday. A communications campaign #THINKB4UCLICK was initiated to get these message across, this took the format of sending information via posters, videos and animations on social media, which were shared with NHS to use and present to getting the message across through traditional channels such as radio and television.
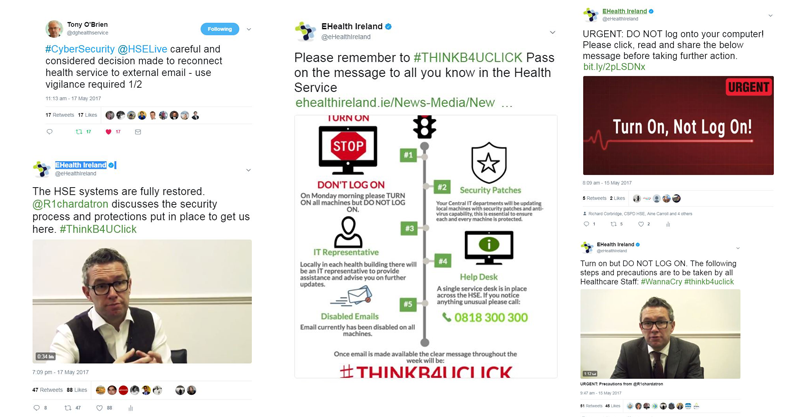
By the end of Monday 15th anti-virus software updates, that addressed the vulnerability exploited by this virus, had been deployed to approximately 52,000 health system PCs and 2,350 servers. In addition newly released Microsoft patches were rolled out to over 28,000 machines. Over half of the 1500 vulnerable Microsoft XP machines had been visited and 1,300 health servers rebooted. The remainder would be visited over the next 48 hours. The teams visited as many sites as possible switching on machines, to allow for patches and updates to be downloaded and hanging information posters before staff returned to work on 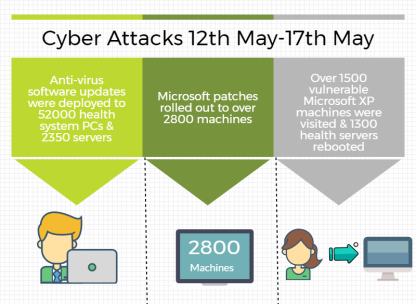
On Wednesday 17th May a plan was
By Thursday 18th May all remote users were back
There was only one incidence of
Since
For example, the 1500 machines running XP are still in the system because they are running very specific programmes linked to pieces of medical equipment (devices that deliver diagnostic imaging (
The entire HSE estate of technology will be reviewed, there were certain systems that were radically overhauled during the MI and steps are being taken to prevent that being necessary again.
There was and is a range of defensive and protective tools in continuous use: anti-spam, encryption, anti-virus, firewalls and other products but this alone was not and will not be sufficient. Since the attack, we have been reviewing all relevant services: How we do business, how we communicate, where the weaknesses in the estate are, how we can patch quicker and again, our security policies and practices and detection protocols.
Partners
This was the first major test of the critical incident management service, introduced in 2016. This team were at the centre of the response to the attack and collaborated with the wider HSE to protect the information systems. There is no doubt that we need to continue to be vigilant for these types of attacks. This MI was a major learning curve and the lessons learned have been taken on board. Moving forward there is an increase in planning to prepare for these types of incidents both in the medium term and long term.
It was a team effort from the entire HSE that responded to this attack, people went above the call of duty to help from the Director

Since the attack, we are encouraging all staff to avail of our Good Information Practices Module. You can find out more about it
- Ambulance Arrivals Project A Case Study
- SNOMED National Release Centre (NRC)
- SVUH Award winning Patient Flow Whiteboard
- Scan for Surgery
- Hospital-based care
- Digital Natives Sign App
- Digitisation of risk assesment tools for Adult mental health services in north Dublin
- Patient Engagement Operating Systems - Hep C
- Digital Transition for HSCPs at St. James's Hospital
- Primary Care Centre Castlebar Case Study
- Mario - Managing active and healthy ageing using caring service robots
- Claimsure - Health Insurance Claims Management System
- Cyber Attack Response
- Data systems in SVUH Emergency Department
- Electronic Discharge Prescription Pilot
- Epilepsy EPR
- eReferral
- eReferral Radiology Pilot
- eRostering
- Electronic Blood Tracking
- GP Practice Management Systems
- Healthmail
- Heart Failure Virtual Clinic
- Infrastructure - MPUP to ECAM
- IT Security - Small changes, big difference
- Kidney Disease Clinical Patient Management System
- Local Asset Mapping Project at St James' Hospital
- LUCY
- Mi Kidney App
- Model Community
- NCHD - Employment Record Portal
- Nursing & Midwifery Quality Care Metrics
- Ophthalmology Electronic Patient Record
- PharmaBuddy
- Radiology & Electronic Patient Record
- National Smart-Pump Drug Library of Paediatric and Neonatal Standardised Concentration Infusions
- Quality & Patient Safety
- Robotic Assisted Surgery Programme
- Shared Learning on EHR
- St. James' Hospital - National Haemophilia System
- Tallaght Hospital Pharmacy
- Tallaght Hospital Patient Engagement App
- Track & Trace
- Using IT to Improve Ireland's Public Sector Healthcare
- National Audiology Clinical Management System (NA-CMS)
- St Vincent's University Hospital Award Winning Whiteboard Patient Flow System
- Snomed Case Study
- Telehealth Project Donegal
- St Vincent's Whiteboard Patient Journey System a Case Study
- Ambulance Arrivals Project
